🟥 SDN THREATWIRE - HOMELAND ATTACKERS: HOW THEY OPERATE ON AMERICAN SOIL
ThreatWire Brief | Powered by CarniVault
October 25, 2025
🧠 BLUF
Jihadist operators on U.S. soil aren’t “sleepers”—they’re active specialists working tasks under legitimate covers. Cells leverage welcome points, pre-arranged jobs, and community integration to blend until activation. Placement follows their skill set (VBID near fabrication nodes; aviation bombers near hub airports). Detection hinges on pattern awareness and inter-agency data fusion, not crude profiling.
Keep reading below …
DISCLOSURE: This post contains affiliate links. If you make a purchase through them, we may earn a small commission at no extra cost to you. This helps keep our work independent. Thank you for your support.
📡 CONTEXT
Former CIA targeting officer Sarah Adams (@TPASarah) outlined on The Dr. Rutherford Show (Ep. 61 “Three Times 9/11”) how foreign-trained militants enter, integrate, recruit, and prepare for attacks inside the United States. Her account describes a pre-wired ecosystem: logistics hubs on arrival, employment covers ready, tasking underway, and local recruitment to expand capability—all while maintaining deep cover across diverse, urban environments.
DISCLOSURE: This post contains affiliate links. If you make a purchase through them, we may earn a small commission at no extra cost to you. This helps keep our work independent. Thank you for your support.
⚠️ THREAT PROFILE
Purpose of the initial phase: establish, staff, and camouflage a functional attack network before the “go” signal.
Welcome points: pre-arranged entry hubs that provide housing, documents, comms.
Pre-set covers: jobs and community contacts are lined up in advance.
Domestic recruitment: residents added for technical/logistics/cyber roles (paid or ideological).
Active tasking: IED fabrication, surveillance, comms, counter-intel—not dormant “sleepers.”
Urban integration: placement in diverse metros to avoid pattern detection.
Skill-based geography: VBID makers near industrial nodes; aviation operatives near hub airports; command in metro centers with secure comms.
If this information helps you, please consider a paid subscription …
🧍♂️ FOR EVERYDAY AMERICANS — THE SINGLE OBJECTIVE: GET OFF THE X
“Off the X” = out of the kill zone and out of predictable patterns.
Move with purpose: increase distance quickly; avoid chokepoints and glass lines.
Shelter smart: lock into interior rooms; identify secondary exits in public venues.
Assume a second phase: expect additional attackers/IEDs; render aid only when the scene is clearly secure.
Report patterns, not people: suspicious surveillance, repeated loitering, parked vans with unchanged positions, unusual probing questions.
Digital discipline: no live-streams during unfolding events; they aid adversary coordination.
Know who’s who: verify LE via badges/vehicle markings; beware of imposters.
Carry essentials: ID, charged phone, tourniquet/IFAK, small water—on your person, not in a bag you’ll drop.
Keep reading below …
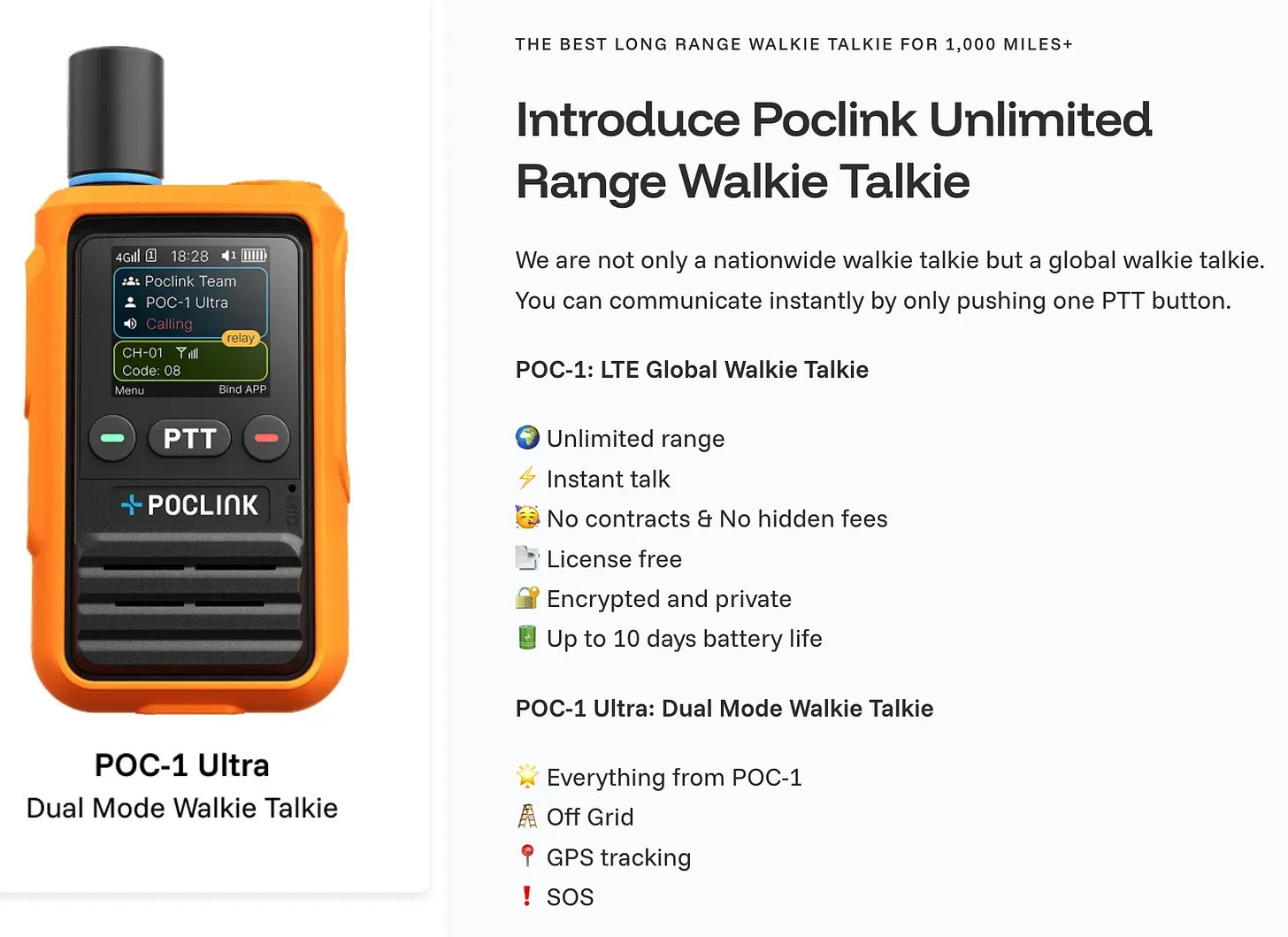
Get the POC-1 Ultras for only $399 for two radios and no annual fee for LTE network service for the life of the radios. This price is only for the first 1,000 units sold. After that they’ll be $1,140 a pair, and $29 to $65 a year for LTE service. Get them HERE.🔊 FEATURED OFFER / GEAR BLOCK (Optional)
Preparedness Essentials — Partners We Trust
Why here: communications, medical, and protective equipment save lives in the first minutes.
Consider vetted options for training tools, carry gear, and protective equipment.
👮♂️ FOR LAW ENFORCEMENT — PRACTICAL ADJUSTMENTS
Targeting mindset: assume your presence, patterns, and facilities are collected on pre-incident.
Arrival control: watch for welcome-point indicators—group move-ins, unusual doc facilitation, cluster housing with identical work covers.
Pattern busting: vary routes, shift times, parking; avoid routine staging that invites VBID placement.
Skill-map your AO: identify fabrication-capable industrial zones, storage yards, self-storage corridors, and hub-airport perimeters.
Pre-attack signatures: long-dwell vehicles, repeated static surveillance at ingress/egress, Wi-Fi/cell anomalies near sensitive sites.
Comms discipline: assume open-source and scanner monitoring; use brevity/coded phrasing.
IED posture: perimeter-first, layered standoff; treat all suspected devices as HAZMAT; call EOD—no ad-hoc render-safe.
Recruitment leads: follow money/ideology vectors—short-term cash workforces, rideshare clusters, “community group” fronts, sudden arrivals with identical employment.
Misinformation control: single spokesperson, rapid rumor correction; anticipate manipulation during incidents.
Fusion & referrals: push suspicious-activity reports to JTTF/Fusion Center early; crosswalk tips with skill-based placement indicators.
If this information helps you, please consider a paid subscription …
🧠 SDN ANALYSIS — JON WHEATON
These aren’t ghost stories—they’re process steps for a quiet war run in neighborhoods like ours. Entry → Welcome Point → Employment Cover → Tasking is the spine of the playbook. The counter is pattern awareness: spot the routine that doesn’t fit, the story that can’t carry weight, the vehicle that never seems to move. This is not fear—it’s disciplined attention, reporting, and preparation.
GodSpeed
Jon Wheaton





This is a HOT discussion lately…thank you for your insight and detail on this topic.
Great brief. Thank you!